Access tokens
Access tokens provide flexible and secure ways to interact with the DataHUB, including synchronization of ARCs from local computers or servers. In most scenarios, users do not have to create access tokens themselves, since ARCitect and ARC Commander take care of this.
When to use access tokens
Section titled “When to use access tokens”- Upload of very large data or large amounts of data. The default access tokens used by ARCitect and ARC Commander expire after two hours. For data uploads that take longer than two hours, users need an access token.
- ARCs stored on a (shared) server. When collecting many ARCs with different scopes on a central server and accessing these ARCs from different machines (office desktop, workstation, laptop), it may be easier to handle the synchronization rights between that server and the DataHUB via tokens. This is a common scenario in core facilities. In this case, we recommend to use group or project access tokens during ARC synchronization to be independent of the current user working on the ARC (via ARCitect or ARC Commander).
- See other advanced examples here.
How to use access tokens
Section titled “How to use access tokens”- ARCitect: Open the
DataHUB Syncpanel and follow the help menu (activated in “Settings”). - ARC Commander: Follow this guide.
| Token Type | Scope of access | Generation |
|---|---|---|
| Personal Access Token (PAT) | User-level (All ARCs of one user) | Generated in user profile settings |
| Group Access Token | Group-level (All ARCs within one group) | Generated in group settings |
| Project Access Token | Project-level access (One specific ARC) | Generated in ARC settings |
Token information
Section titled “Token information”When creating a new access token, users are asked to adapt or fill out some information summarized here.
Choose a descriptive name. This helps to track its usage and identify it later, especially if multiple tokens are created. This could for instance be the computer (“Office Desktop”) or Application (“ARCitect Office Desktop”) where the token is used.
Token description (optional)
Section titled “Token description (optional)”You can add a more detailed description about the token’s purpose for easier identification.
All tokens support expiration, allowing you to set a time limit on their validity. This is essential for maintaining security and reducing the risk of token misuse over time. The token expiration defaults to one month in the future. You can adapt or remove the expiration date, e.g. to allow only temporary or long-time access.
You can assign a role for the access tokens (only group and project tokens).
Together with the role, the scopes define what actions the token can perform. Common scopes include:
- api: Full access to all features
- read_repository: Read access to repositories
- write_repository: Write access to repositories
Each token type may have different available scopes based on its level (user, group, project).
Creating an access token
Section titled “Creating an access token”-
Sign in to the DataHUB
-
Open your Project (ARC)
-
Navigate to the ARC’s settings
-
Open the
Access Tokenssettings in the sidebar(1) -
Enter or adapt the required token information
(2)(more about token information here) -
Click
Create project access token (3)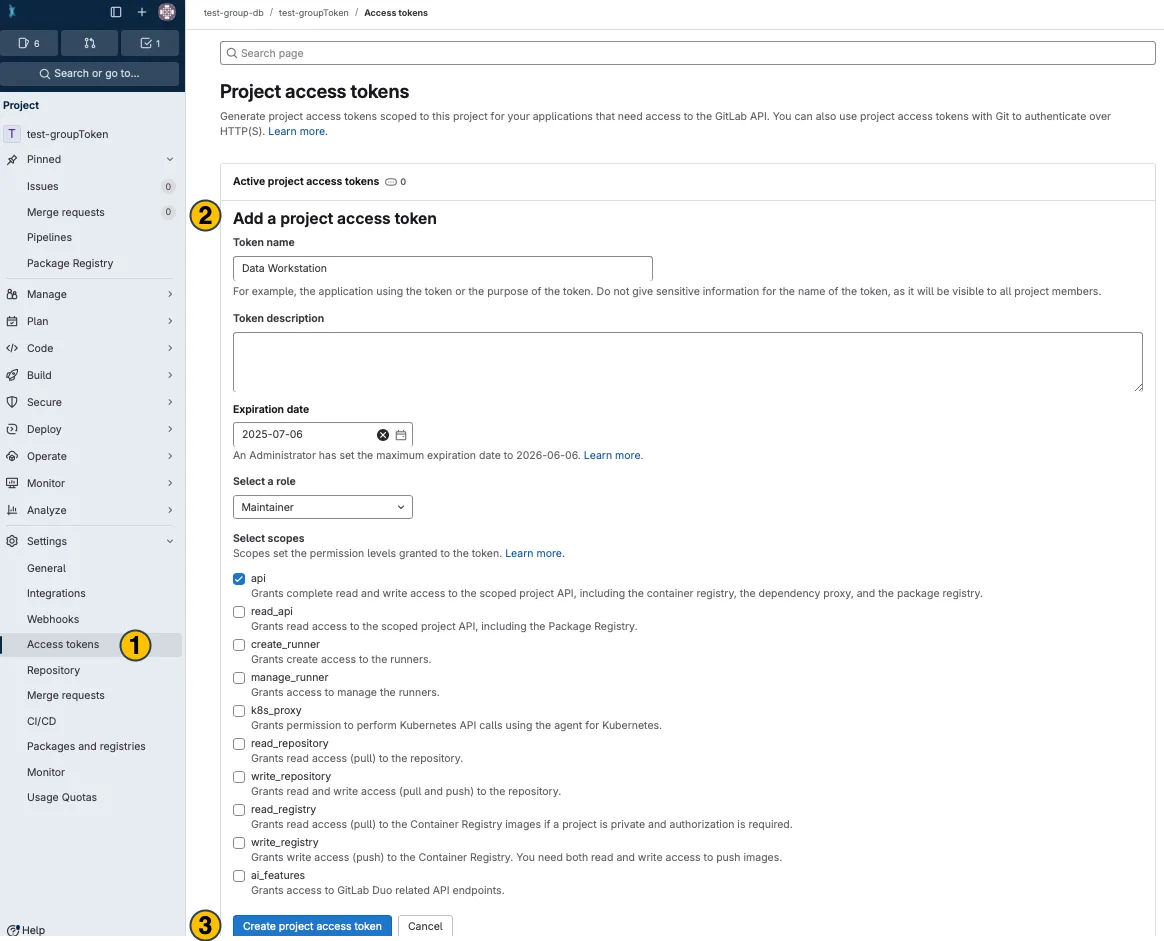
-
Your new project access token appears on top. Copy (4) and use it in the desired application.
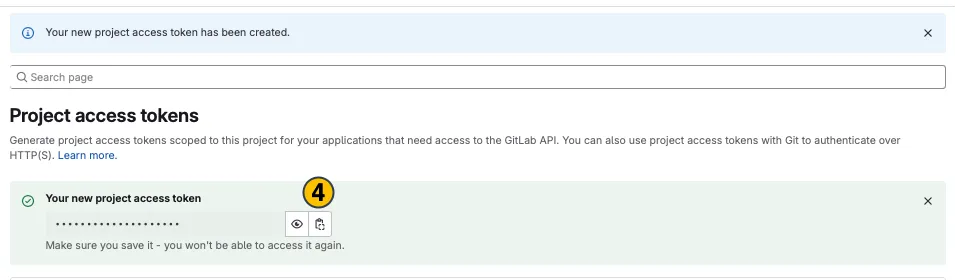
-
Sign in to the DataHUB
-
Navigate to the group’s settings
-
Open the
Access Tokenssettings in the sidebar(1) -
Enter or adapt the required token information
(2)(more about token information here) -
Click
Create group access token (3)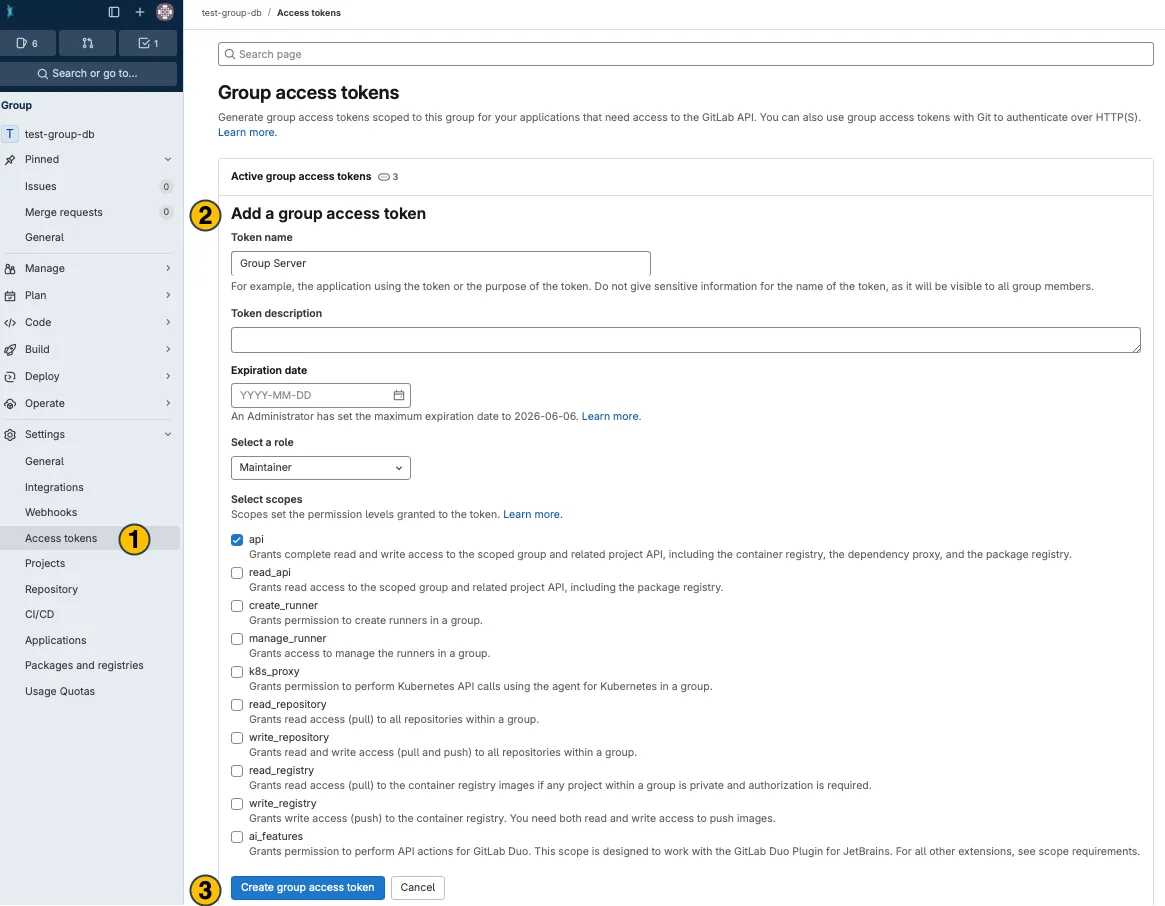
-
Your new group access token appears on top. Copy
(4)and use it in the desired application.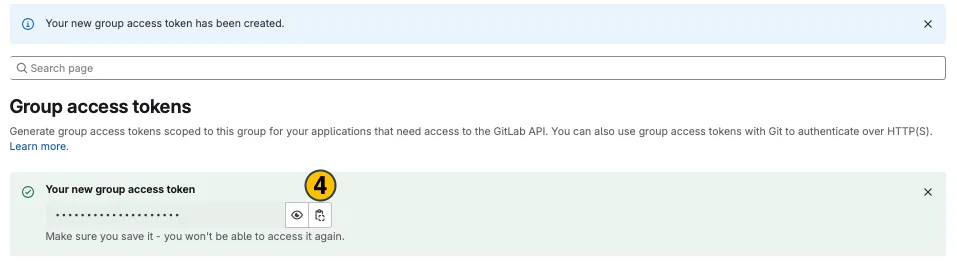
-
Sign in to the DataHUB
-
Navigate to your user settings
-
Open the
Access Tokenssettings in the sidebar(1) -
Enter or adapt the required token information
(2)(more about token information here) -
Click
Create personal access token (3)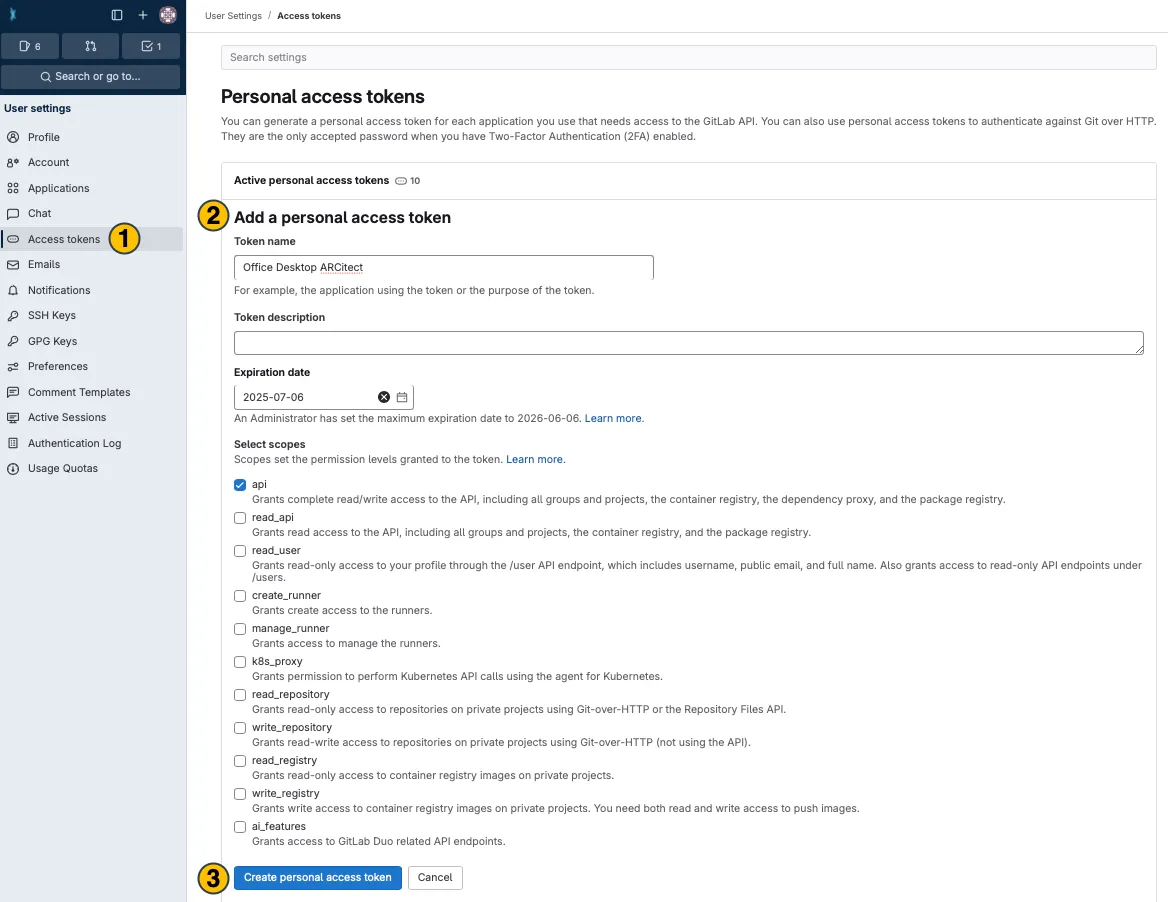
-
Your new personal access tokenappears on top. Copy(4)and use it in the desired application.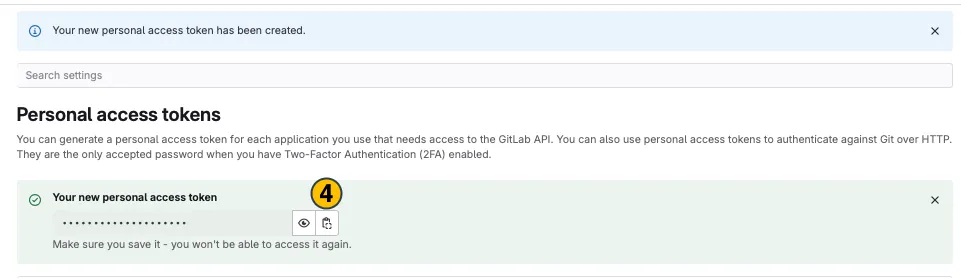
Security & Revoking access tokens
Section titled “Security & Revoking access tokens”Depending on the chosen type (user, group, project) of token as well as its role and scope, an access token grants access to varying degrees to one or multiple ARCs.